The September 2025 Patch Tuesday was intended to bolster the security of the Windows 11 ecosystem, specifically targeting vulnerabilities within the servicing stack. However, for many system administrators and home office users, the KB5065426 update brought an unexpected and disruptive side effect: the complete collapse of local network file and print sharing.
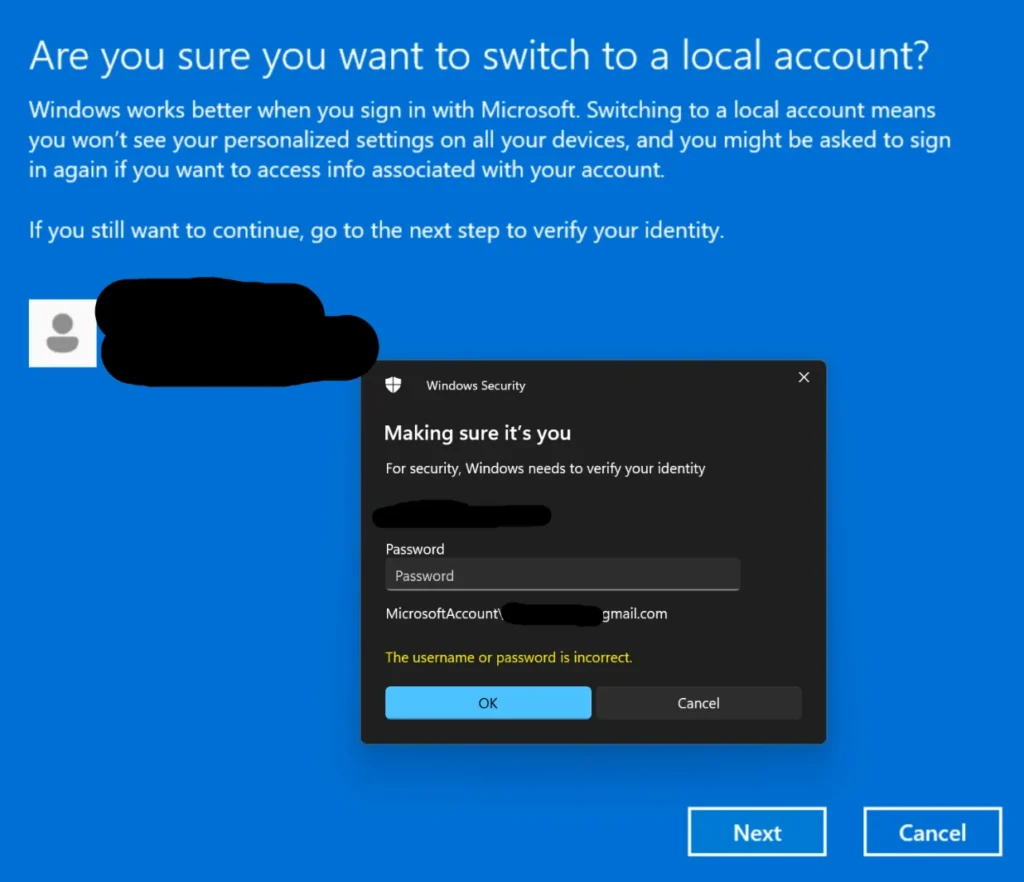
Users are reporting a persistent “credential loop” where Windows rejects 100% accurate usernames and passwords with the error message: “The username or password is incorrect.” Even more baffling is that this occurs even when “Password Protected Sharing” is disabled or when the user is using a local account that has worked for years.
In this exhaustive guide, we will dissect the technical mechanics of why this update breaks SMB (Server Message Block) connections, the hidden role of the Windows Security Identifier (SID), and how to restore your network functionality without compromising your system’s security.
Key Takeaways: How to Restore SMB Sharing Quickly
If you are in a hurry, here is the executive summary of why your network is broken and how to fix it:
- The Root Cause: KB5065426 introduces strict SMB auditing. It blocks connections between computers with duplicate SIDs (a common issue in cloned systems).
- The “Invalid Password” Loop: This is a security rejection, not a typo. Windows refuses the handshake because the client and host machine identities conflict.
- Immediate Fix 1 (Network Profile): Ensure your network is set to Private, not Public. The update often flips this setting.
- Immediate Fix 2 (Guest Access): For older NAS devices, re-enable Insecure Guest Auth via the Registry.
- The Permanent Fix (SID Regeneration): Use a professional tool like Wittytool Disk Clone or Windows Sysprep to regenerate a unique SID. This resolves the conflict without uninstalling security patches.
Understanding the KB5065426 Conflict
The KB5065426 update (Build 26100.6584) is a cumulative security update for Windows 11, version 24H2. Unlike previous minor patches, this update introduces stricter SMB server-side auditing and hardening for Extended Protection for Authentication (EPA) and SMB signing.
The goal of these changes is to prevent “Man-in-the-Middle” (MitM) attacks and NTLM relay exploits. However, these new security “guardrails” have exposed a long-standing issue in the way many Windows systems are deployed: Duplicate Security Identifiers (SIDs).
When you attempt to connect to a shared folder or a networked printer, the two machines perform an authentication handshake. If the security hardening in the latest update detects an identity conflict – specifically between the client and the host – it terminates the connection immediately, manifesting as a “wrong password” error.
The Core Culprit: The Duplicate SID Problem
To understand the solution, one must understand the Security Identifier (SID). Every Windows installation has a unique machine SID, which acts as a fundamental “fingerprint” for the operating system’s security principal.
Why do SIDs become duplicated?
In a perfect world, every Windows PC is installed from scratch. In the real world, IT departments and enthusiasts use disk cloning or system imaging to deploy Windows across multiple machines quickly.
- If a technician clones “PC-A” to “PC-B” without running a “Generalize” pass (via Sysprep), both computers will have the exact same Machine SID.
- In older versions of Windows, this was a “invisible” problem that rarely affected simple Workgroup sharing.
- KB5065426 changes the rules. The update effectively prohibits SMB/NTLM authentication between two machines that share the same SID. Windows now perceives a connection from a machine with the same SID as a potential security breach or a circular authentication error, leading to the “Access Denied” or “Invalid Password” loops.
Immediate Symptoms and Troubleshooting
Before applying a permanent fix, you should verify if KB5065426 is indeed the cause. Look for these specific behaviors:
- The Credential Loop: You are prompted for a password. You enter it correctly. The prompt disappears for a split second and then reappears, empty.
- System Error 86: If you try to map a drive via Command Prompt (
net use), you may receive “System error 86 has occurred. The specified network password is not correct.”
- Network Profile Flips: Check your Network & Internet settings. Many users find their connection has been reset from “Private” to “Public,” which automatically engages the Windows Firewall to block inbound SMB traffic on Port 445.
- Event Viewer Clues: Check the
Microsoft-Windows-SMBServer/Operationallogs. You might see warnings related to authentication failures or “Duplicate SID detected” in the security logs (Event ID 4625).
Why You Should NOT Simply Uninstall the Update
A common recommendation on tech forums is to simply uninstall KB5065426 via the “Update History” menu. While this restores sharing immediately, it is highly discouraged for several reasons:
- Security Risk: KB5065426 contains vital patches for the Windows kernel and the servicing stack. Rolling back leaves your system vulnerable to known exploits.
- The SSU Bundle: This update is often delivered as a combined Servicing Stack Update (SSU) and Latest Cumulative Update (LCU). Once the SSU is applied, certain system components are permanently upgraded, making a full rollback difficult or unstable.
- The Re-install Loop: Unless you disable Windows Updates entirely, the system will likely re-download and install the patch within 24 to 48 hours.
The Professional Solution: Regenerating a Unique SID
If your network sharing is broken due to a duplicate SID conflict, the only permanent, security-conscious fix is to change the SID on one of the conflicting machines.
The Efficient Method: Professional Disk Utilities
For users who need to maintain their data and settings while fixing the identity conflict, using a professional-grade cloner is the preferred route. Tools like Wittytool Disk Clone integrate a dedicated Windows SID changer feature designed specifically for post-clone environments.
By leveraging a built-in utility to change windows server SID or workstation SID, you can bypass the “Generalize” limitations of Sysprep without wiping user profiles or installed applications. The tool works by scanning the registry hives and security descriptors, systematically replacing the old SID with a brand-new, unique identifier. Once each machine has a distinct SID, the authentication hardening introduced in KB5065426 no longer flags them as conflicting systems, and SMB sharing functionality is immediately restored.
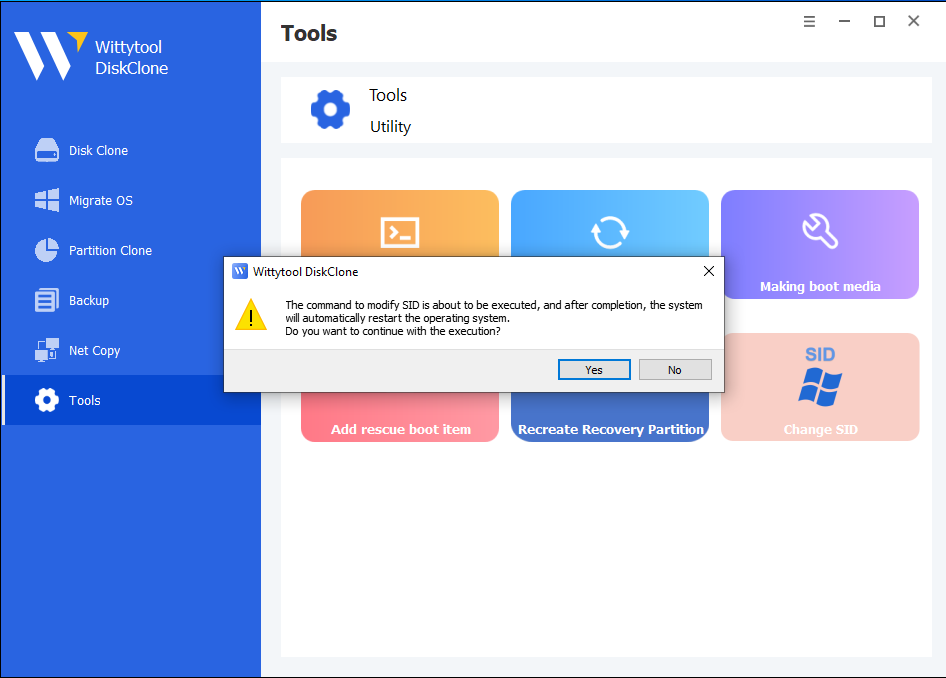
Modify your system SID with a single click. Please follow the steps below:
Step 1: Initiation. Locate “Change SID” and click the “Start” button.

Step 2: Automated Preparation. The program will uninstall applications that may have permission conflicts.
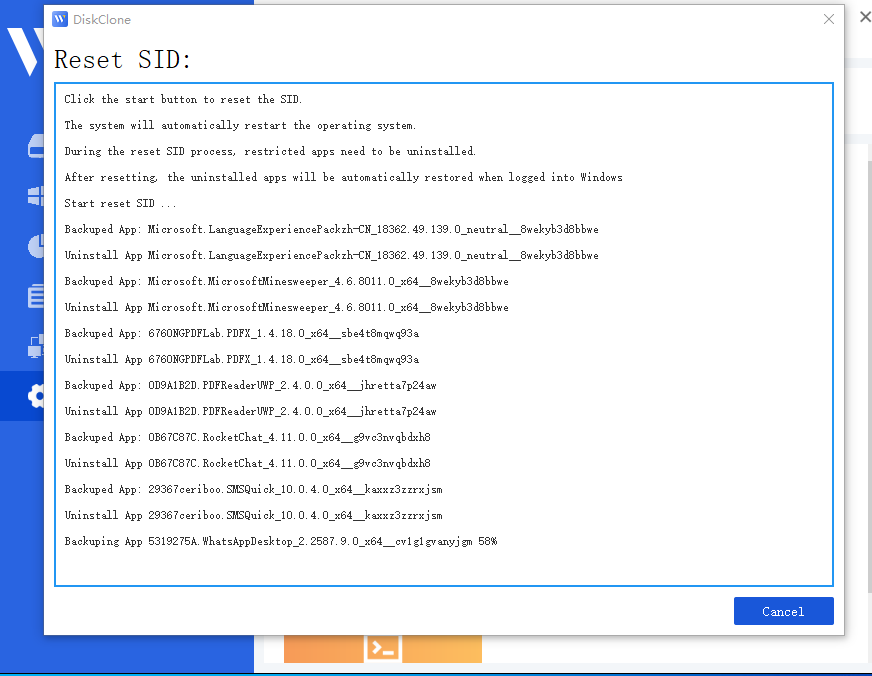
Note: All apps and data are backed up automatically before uninstallation.
Step 3: System Restart. The system will automatically restart to apply the new SID.

Step 4: Automatic Restoration. Upon logging back in, Wittytool Disk Clone will automatically restore the uninstalled programs and their associated data. Once the restoration is finished, the SID modification process is complete.
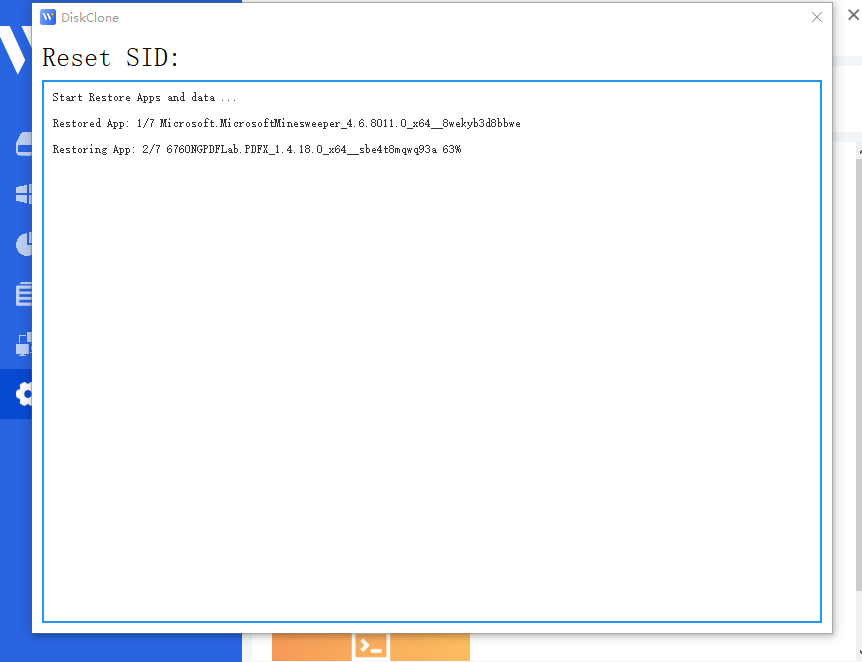
Important Post-Process Notes:
*Computer Name: To avoid network naming conflicts, your computer name will be changed to a random string.
*Local Accounts: Your Windows local accounts and settings will remain unchanged.

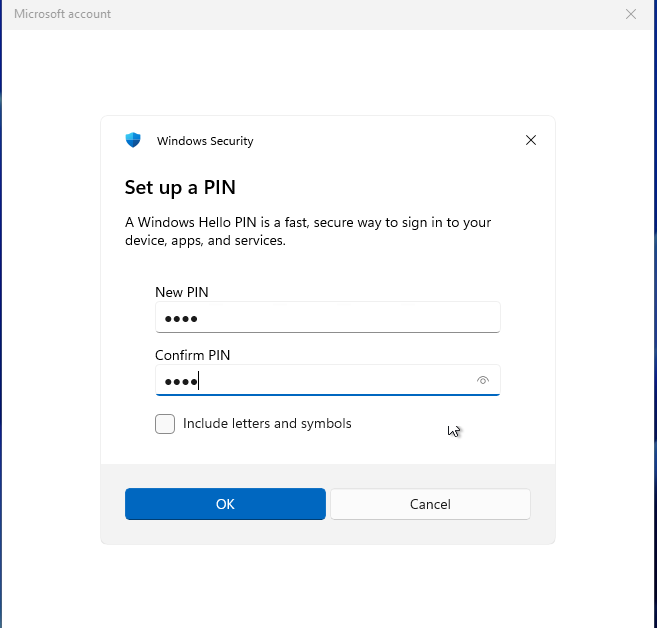
*Microsoft Accounts: If you use a Microsoft account, you will be required to reset your PIN upon your first login after the restart.
Video guide – How to change Windows SID via Wittytool Disk Clone (Full Walkthrough)
The Manual Method: Sysprep
Microsoft provides a built-in tool called Sysprep (located in C:\Windows\System32\Sysprep). Running sysprep /generalize /oobe will reset the machine SID. However, Sysprep is notorious for being “destructive” and fragile:
- It often fails if you have installed Windows Store apps (UWP).
- It resets the “Out of Box Experience,” meaning you may have to re-configure user accounts.
- It can strip out drivers or reset personalized desktop settings.
Alternative Workarounds (If SIDs are not the issue)
If you have verified that your SIDs are already unique (using a tool like PsGetSid), the issue may lie in the specific SMB protocol settings.
Enable Insecure Guest Access
Windows 11 24H2 has further disabled “Insecure Guest Logons.” If your shared folder is on an older NAS or a PC without a password, you may need to re-enable this via the Registry:
- Navigate to
HKLM\SYSTEM\CurrentControlSet\Services\LanmanWorkstation\Parameters. - Create a DWORD value named
AllowInsecureGuestAuth. - Set it to
1.
Check Port 445 and NetBIOS
The update may have disabled NetBIOS over TCP/IP. Ensure that Port 445 (TCP) is open in your firewall and that your network adapter settings have “Enable NetBIOS over TCP/IP” checked in the Advanced WINS settings.
Preventing Future Sharing Issues
To avoid these headaches in the future, your deployment strategy should change. Whenever you move a Windows installation to a new drive or a new computer:
- Don’t just sector-copy: Use an intelligent cloning solution.
- Always ensure identity uniqueness: When performing a migration, utilize the “Change SID” or “Generate Unique Identity” options provided by your software.
- Verify Network Profiles: After any major cumulative update, verify that your network is still set to “Private.”
Using a robust tool like Wittytool Disk Clone during the initial migration phase prevents the “Duplicate SID” trap from ever being set, ensuring that even the strictest Windows security updates won’t lock you out of your own network.
Conclusion
The KB5065426 update is not inherently “broken”; rather, it is more “sensitive” to configuration errors like duplicate SIDs. While it may feel like a bug, it is actually Windows 11 attempting to enforce a higher standard of network identity security.
By identifying the SID conflict and using professional tools to regenerate a unique identity, you can enjoy both a secure, patched system and a functional, high-speed local network. Don’t settle for the “band-aid” fix of uninstalling updates – fix the root cause and keep your Windows environment modern and secure.
FAQ
How can I tell if two of my computers have the same SID?
You can download the PsGetSid utility from Microsoft Sysinternals. Run the command on both PCs in the Command Prompt. If the long string of numbers (excluding the last few digits) is identical, you have a duplicate SID conflict that is likely blocking your SMB sharing after the latest update.
Will changing the SID affect my installed programs or license?
If done through a professional utility like Wittytool Disk Clone, the process is designed to be non-destructive to your files. However, some strictly licensed software (like high-end CAD or certain database servers) and Windows Domain joins may require a re-authentication or a rejoin to the domain after a SID change, as they rely on the SID for identity.
Can I just create a new user account to fix the KB5065426 error?
Generally, no. A new user account creates a new “User SID,” but the underlying “Machine SID” remains the same. Since the SMB authentication failure in this update often happens at the machine-trust level, a new user account will usually encounter the same “Invalid Password” loop.
Is it safe to stay on an older version of Windows to avoid this?
Staying on an unpatched version of Windows 11 is not recommended. SMB vulnerabilities are a primary target for ransomware (like the infamous WannaCry). It is much safer to fix the identity conflict (SID) and keep the security improvements provided by the KB5065426 update.

